Security the Basics
Lesson 11: Encryption – Authenticated Encryption (seclib)
Normally, when something is encrypted it is secret, but it is not really protected from being manipulated. Authenticated encryption not only provides sypher text, it also provides an authentication tag, which can be used to verify that the data is not being manipulated or damaged.
- Press F5 to run SymKeyEncrypt.vs. From the application screen, select VIEW from the top menu and then AUTHENTICATED ENCRYPTION.
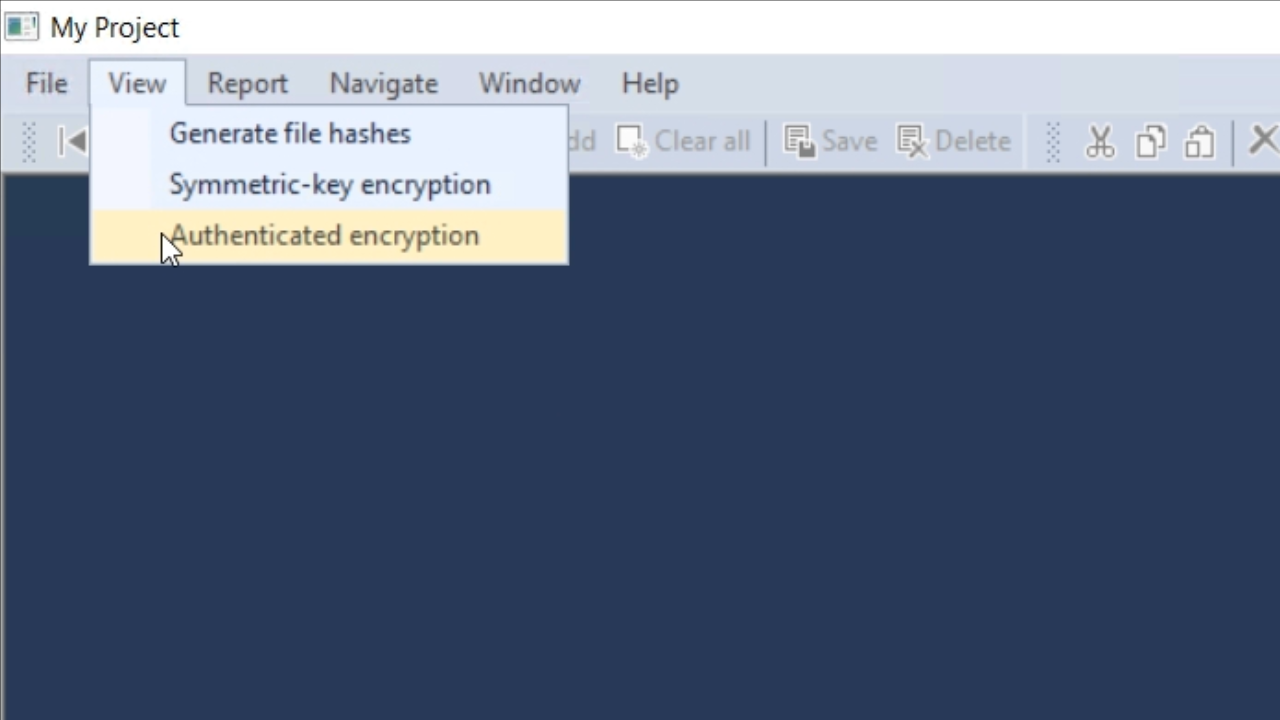
- This view is similar to those in previous lessons, but there are some differences. The ‘IV’ field has been replaced with ‘Nonce,’ which is nearly the same. There is a new field, ‘AAD,’ that is not currently important. The ‘Tag’ field, however, is important, and is the field for the authentication tag.
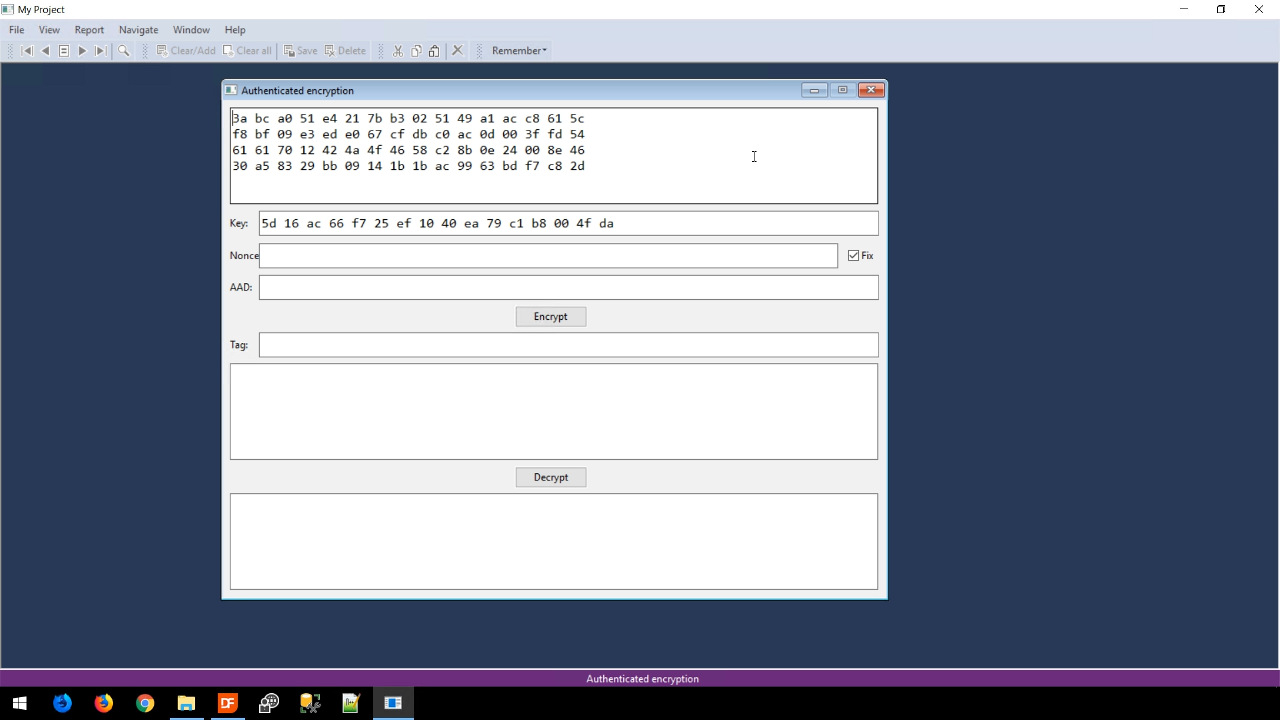
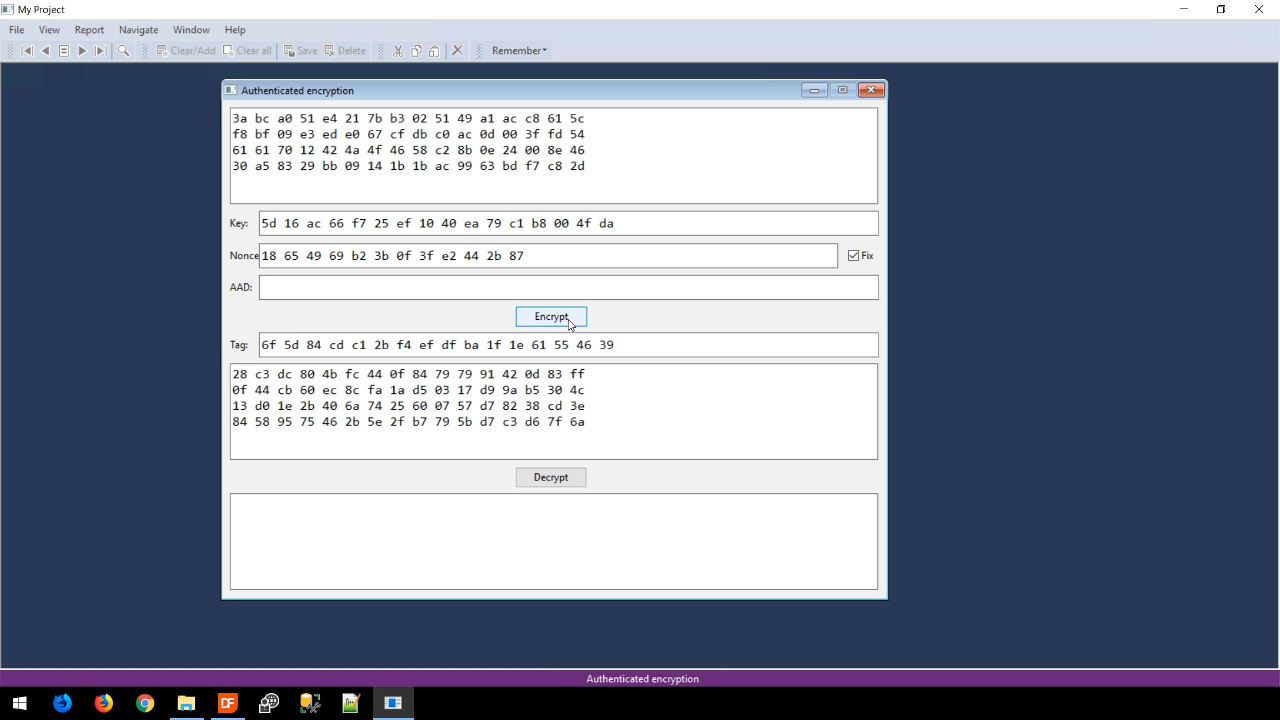
- Pressing ENCRYPT creates four lines of sypher text data and an authentication tag.
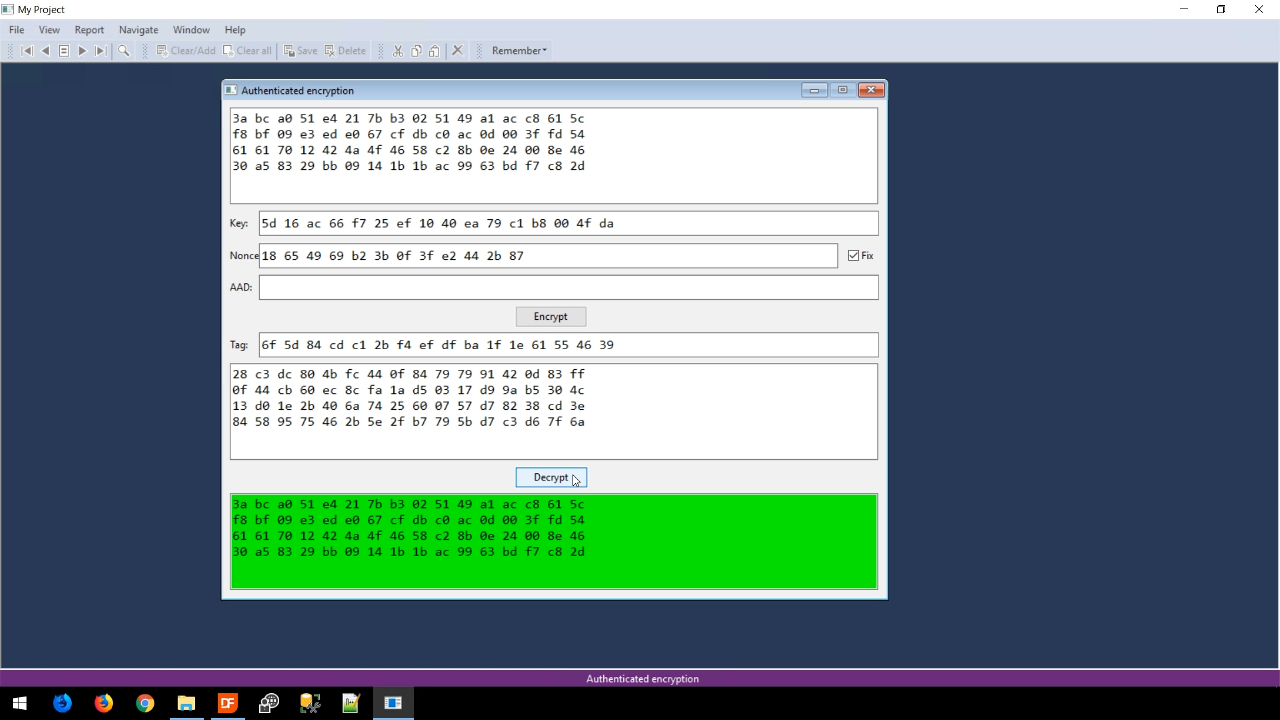
- Pressing DECRYPT outputs the original data with a green background. The green indicates that the data is fine. An additional function called, hAuthentic, can be called in the code to say ‘yes’ or ‘no’ to check the code.
- If the encrypted code is changed at all and the DECRYPT button is pushed, not everything will be decrypted, and the background will be red. The ability to tell the difference between valid and invalid data is possible because of the authentication tag.
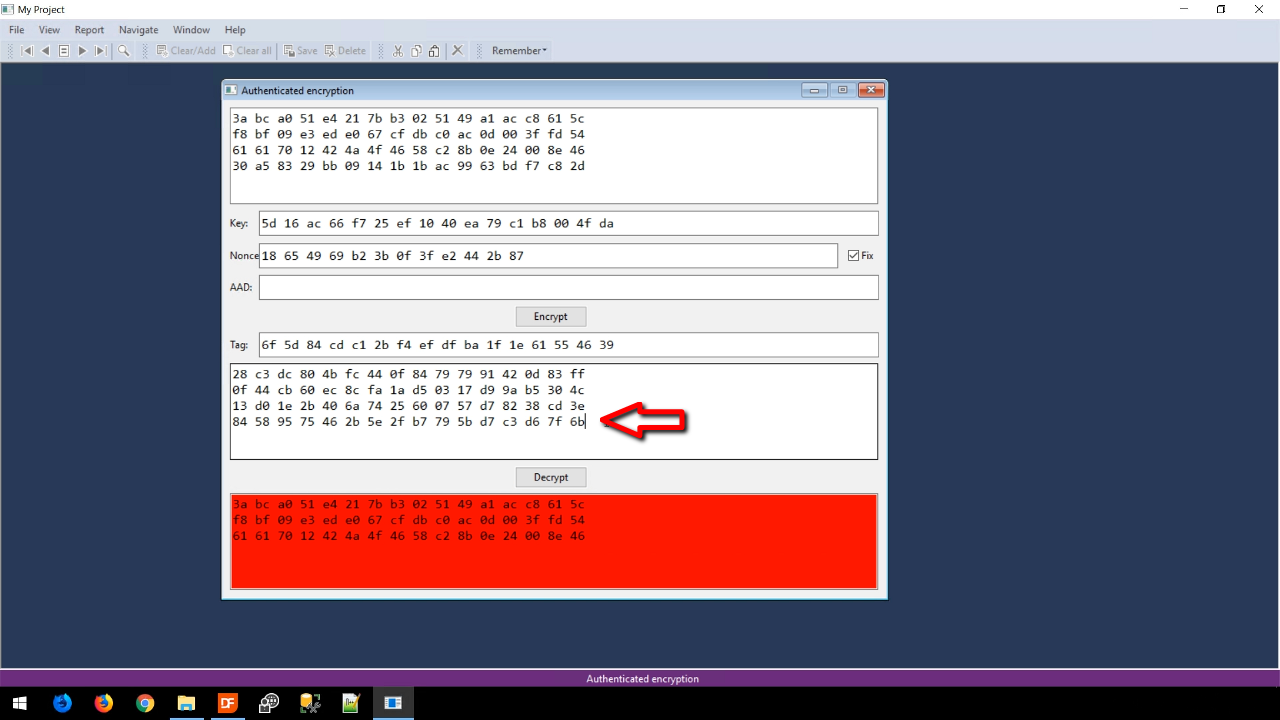
- Changing the tag and pressing DECRYPT will also result in the data being flagged as invalid by presenting a red background.
- The Nonce field – The Nonce is a random part of the initialization vector (IV). The specific algorithm being used in the example is AES with the block mode called GCM. This block mode is an authenticated encryption block mode that will append a counter-value to the nodes.
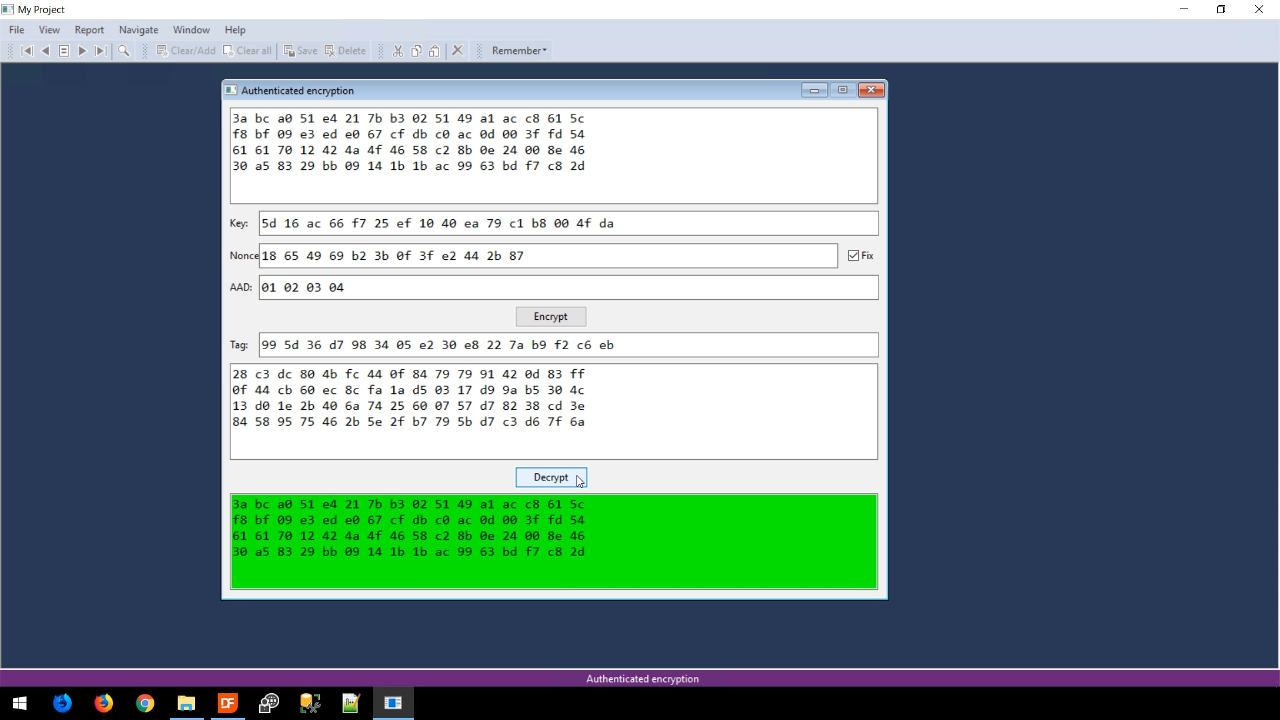
- The AAD field – Occasionally, it is necessary to also verify that included plain text, such as a header, is also valid. If the plain text is added to the algorithm it will not be encrypted, but it will be part of the authentication tag. For example, if four bytes of plain text, “01 02 03 04,” is added to the AAD field and ENCRYPT is pressed, the authentication tag will change, but the cypher text will remain the same. Pressing DECRYPT shows the validated original data.
- CHALLENGE – Create a new view that will open a file that will be encrypted using authenticated encryption with a fixed key. Then have a way to have the file flagged if the data has been tampered with.





