Security the Basics
Lesson 6: DataFlex Security Library Overview
The DataFlex Security Library is a collection of three libraries. There is a base library that contains the abstract classes that are implemented by the others. There is library for the Cryptoapi Next Generation (CNG) encryption engine, which is a library of encryption routines that are available within Windows. Lastly, there is a library for libsodium, which is an external DLL containing more recent and advanced algorithms.
The libraries also have multiple layers. The bottom layer is the engine layer, which is the library itself. Above that layer, are two or three abstraction layers, which translate the common API for the security API to the engine-specific APIs. The final layers are high level layers, which are task-based abstractions.
Libsodium requires some extra dependencies installed. It needs the DLL itself as well as the Visual C++ Runtime.
Demonstration
- What needs to be included to use the DataFlex Security Library? The first thing is the DFSecurity.pkg, which is the main package for the security library. It exposes the interfaces that the engines use.
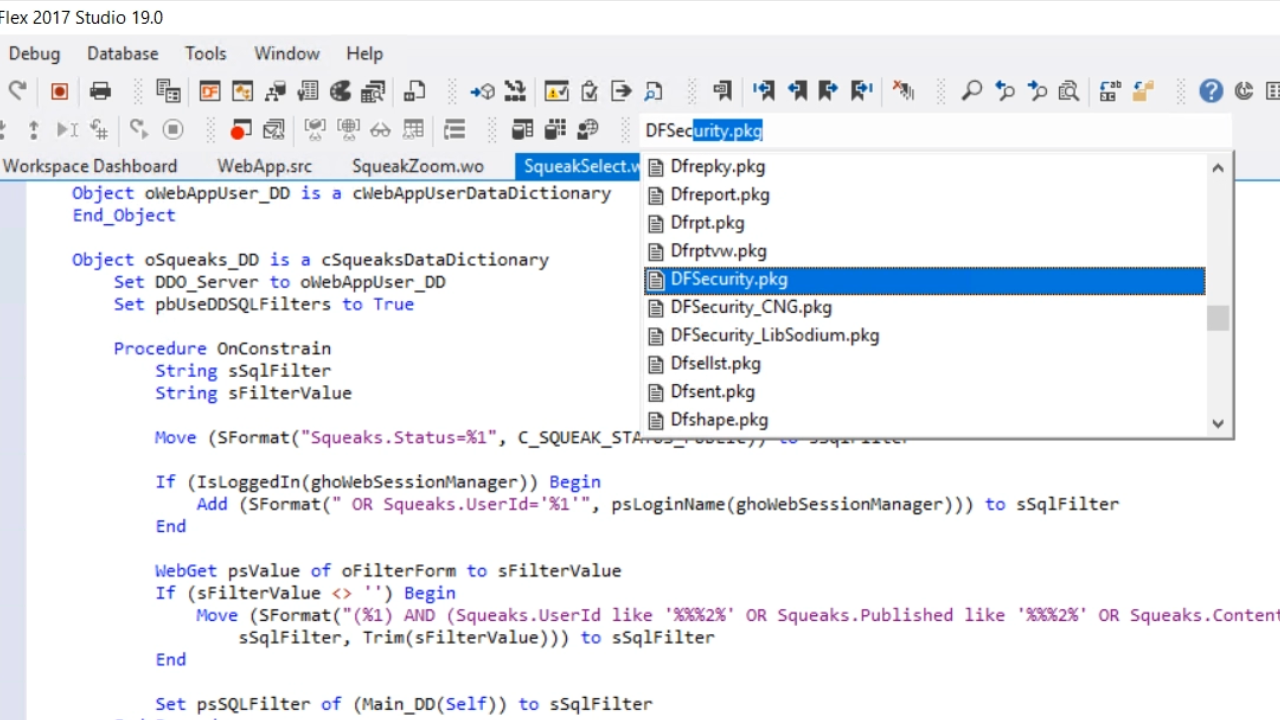
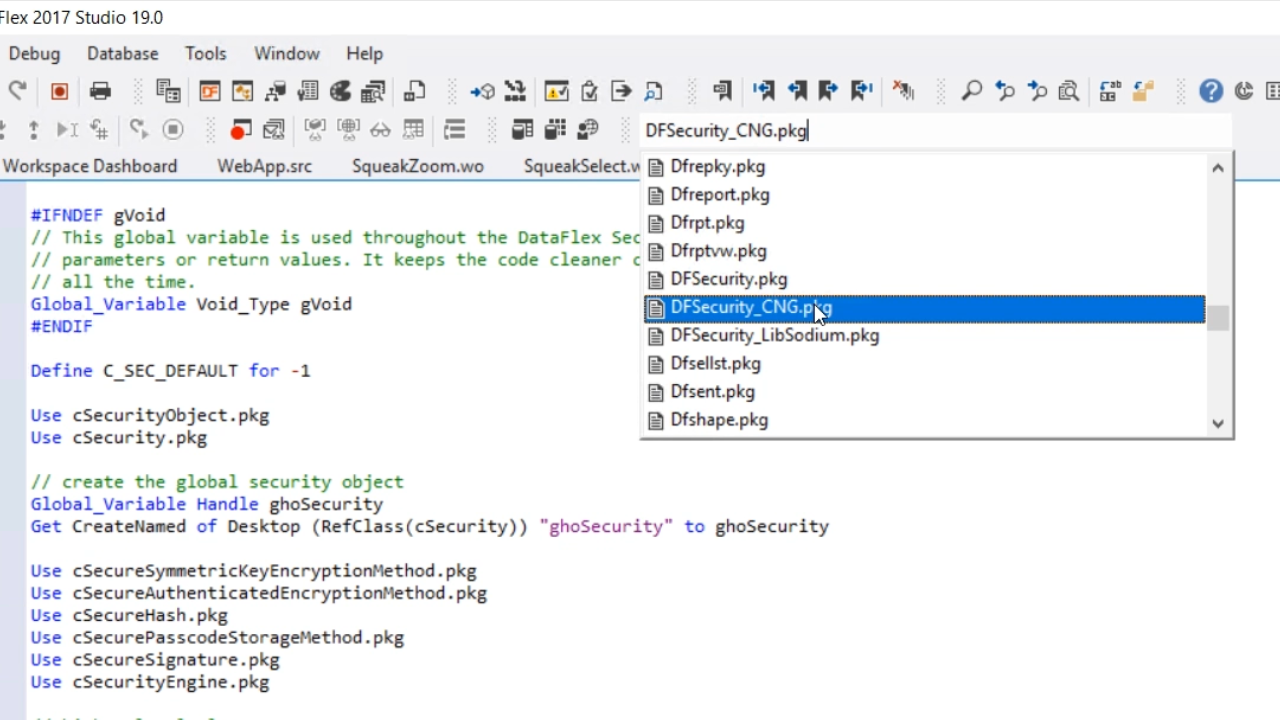
- Initially, it does not have any real functionality when first applied, so another package, either DFSecurity_CNG.pkg or DFSecurity_LibSodium.pkg, is needed. These two packages include all the real functionality for a single engine. DFSecurity_CNG.pkg is used in this demonstration.
- DFSecurity.pkg includes several basic classes. One such class that is worth looking at is the cSecurity.pkg (to view its definition, right click on ‘cSecurity.pkg’ in the code, and select ‘Go to Definition’).
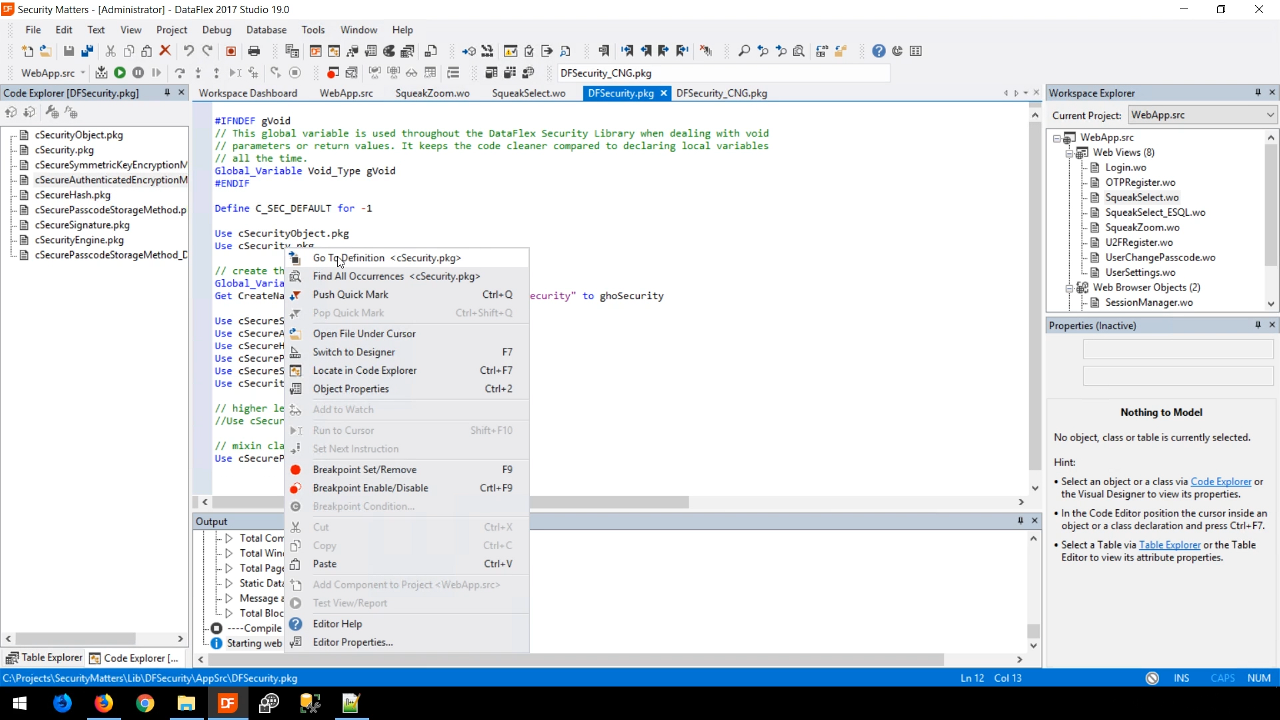
- This is because when including DFSecurity there is one global object called ‘ghoSecurity.’ This object can be called on many occasions with necessary functionality.
- To look at its last function, expand ‘cSecurity’ in the ‘Code Explorer’ panel on the left, and select ‘RandomData.’
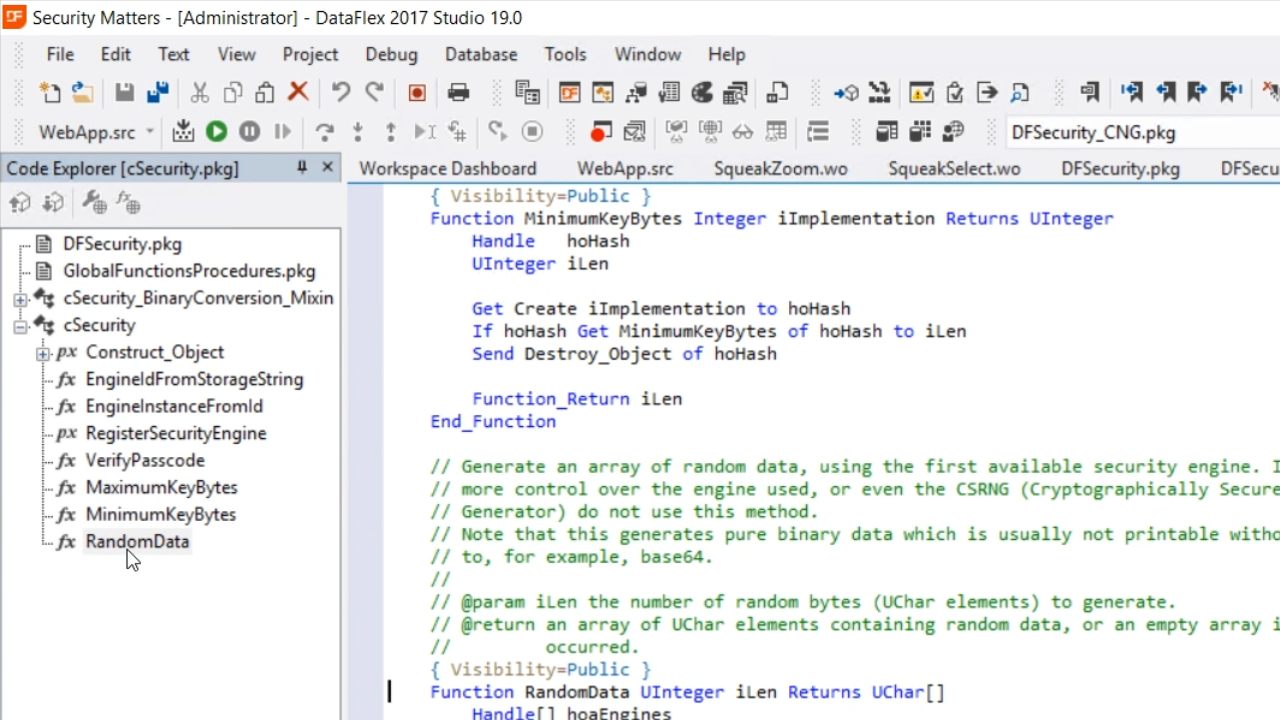
- A lot of random functions return random data, but that is not necessarily cryptographically secure. The RandomData function returns binary data that is truly securely random, which is needed for cryptology. Note that the entire library uses UChar arrays for most function calls because they are real binary data. If strings were supported, for example, there would be encoding issues.
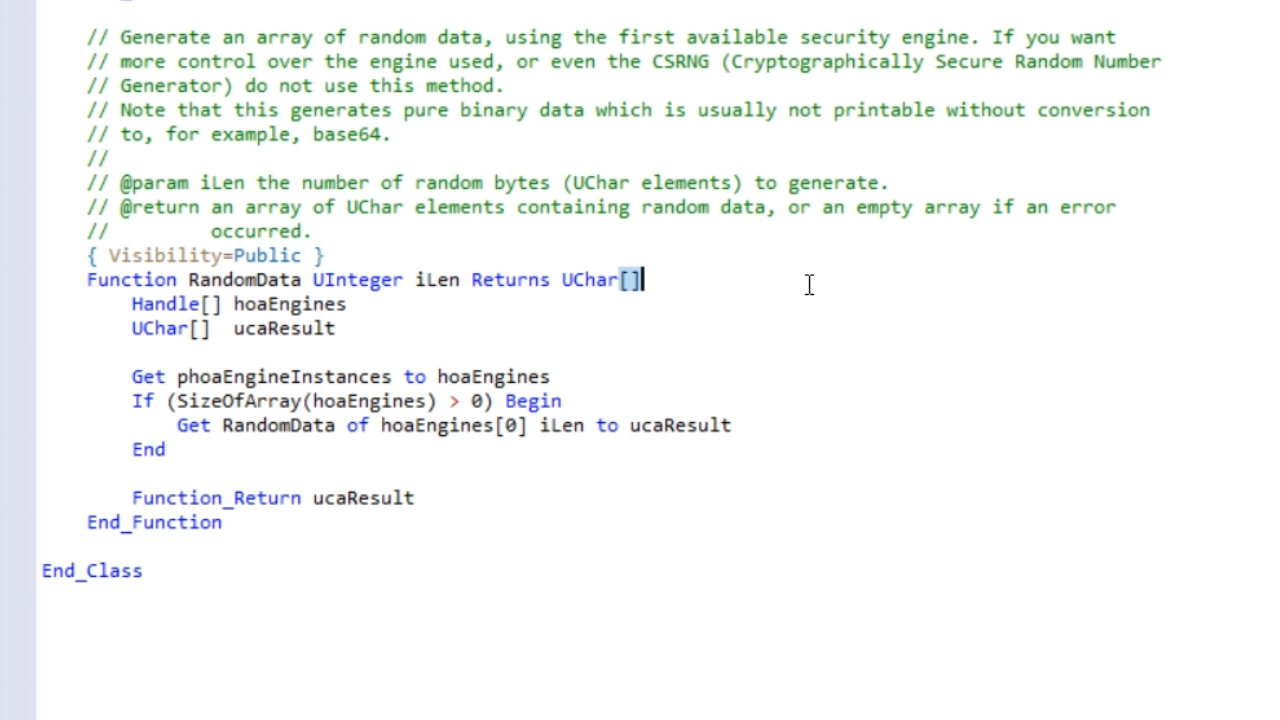
- If the binary data needs to be saved or retrieved from the database or a file, it most likely needs to be converted. There is an entire mixing class that has functions for that. Expanding the ‘cSecurity_BinaryConversion_MixingClass’ from the ‘Code Explorer’ panel on the left to expose the many mixing functions.
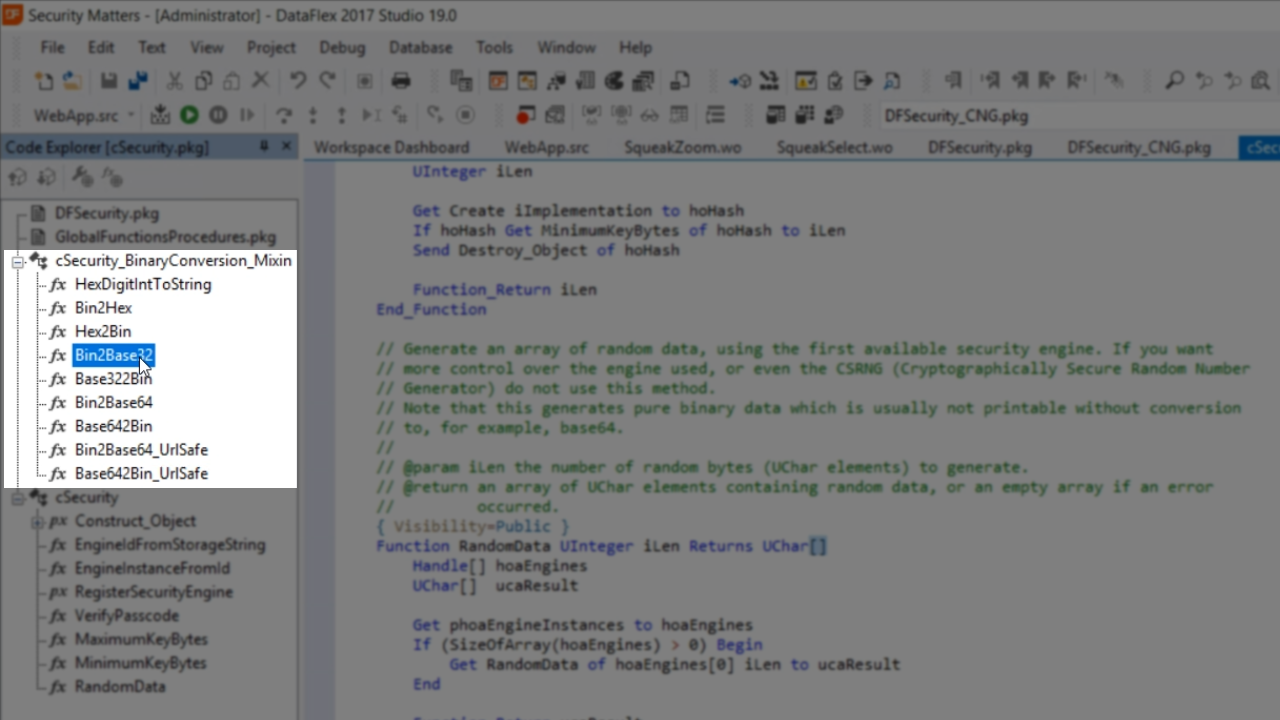
- There are two methods for the ghoSecurity object: MinimumKeyBytes and MaximumKeyBytes. These can be found in the ‘Code Explorer’ panel by expanding ‘cSecurity. They are both utility functions that are not necessarily needed but can be used to identify what the minimum or maximum number of bytes are needed for a key in an encryption algorithm or hash.
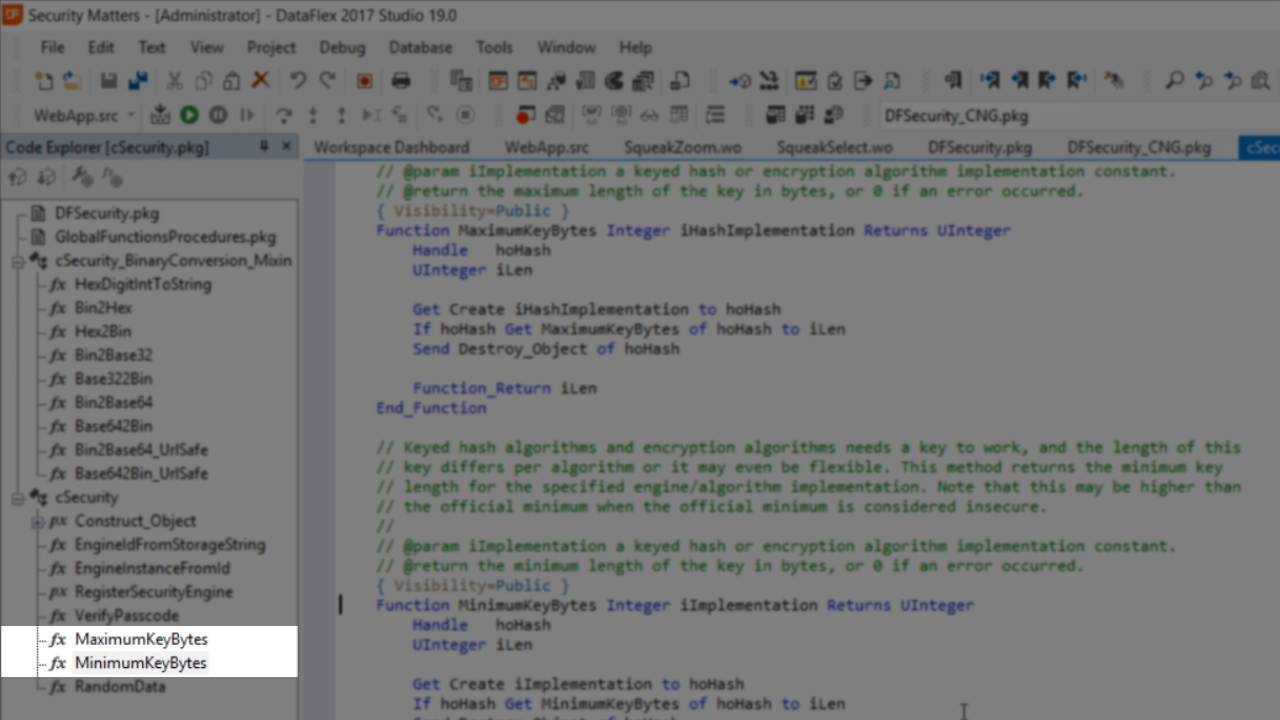
- More advanced items can also be found here, but they are not in the ghoSecurity object. The class shown here is a sub class of the ‘cSecurityObject’ class.
- Right clicking on ‘cSecurityObject,’ and select ‘Go to Definition’ to view its definition. The definition shows several items that are in most of the classes in the security library.
- In the Construct-Object, the Delegation_Mode is set to No-Delegation. This means that if a message is sent to an unknown security object an error will result. The layers of parent objects above it will not be tried. This is intentional so that passwords or plain text data are not leaked to different objects.
- SecureStringOverwrite and SecureUCharArrayOverwrite methods are also in place, so that keys and passwords in memory are securely overwritten before the release of the data.