Users often choose bad passcodes. There are certain things that can be done to force them to create stronger passcodes. Examples would be requiring a minimum length and checking passcodes against databases of leaked codes. There are several resources on the internet for checking for leaked codes, but one of the most common is haveibeenpwned.com. This site has a file that can be downloaded that contains over five million breached codes.
A file has been added to the workspace that contains the first 100,000 most commonly used passcodes from haveibeenpwned.com.

To import the password hashes from haveibeenpwned.com. Select ‘PwnedPasswordsImport.src’ as the current project in the ‘Workspace Explorer’ on the right and run it.
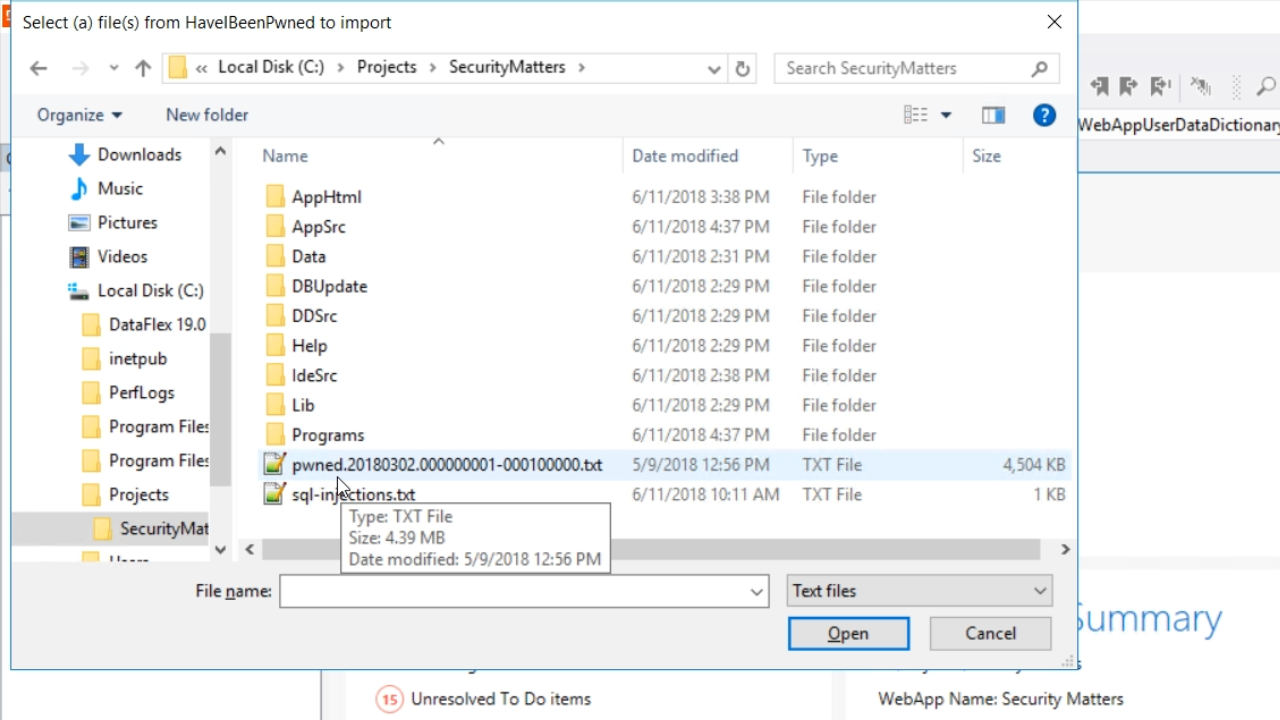
Next open the pwned file from the root directory of ‘SecurityMatters.’
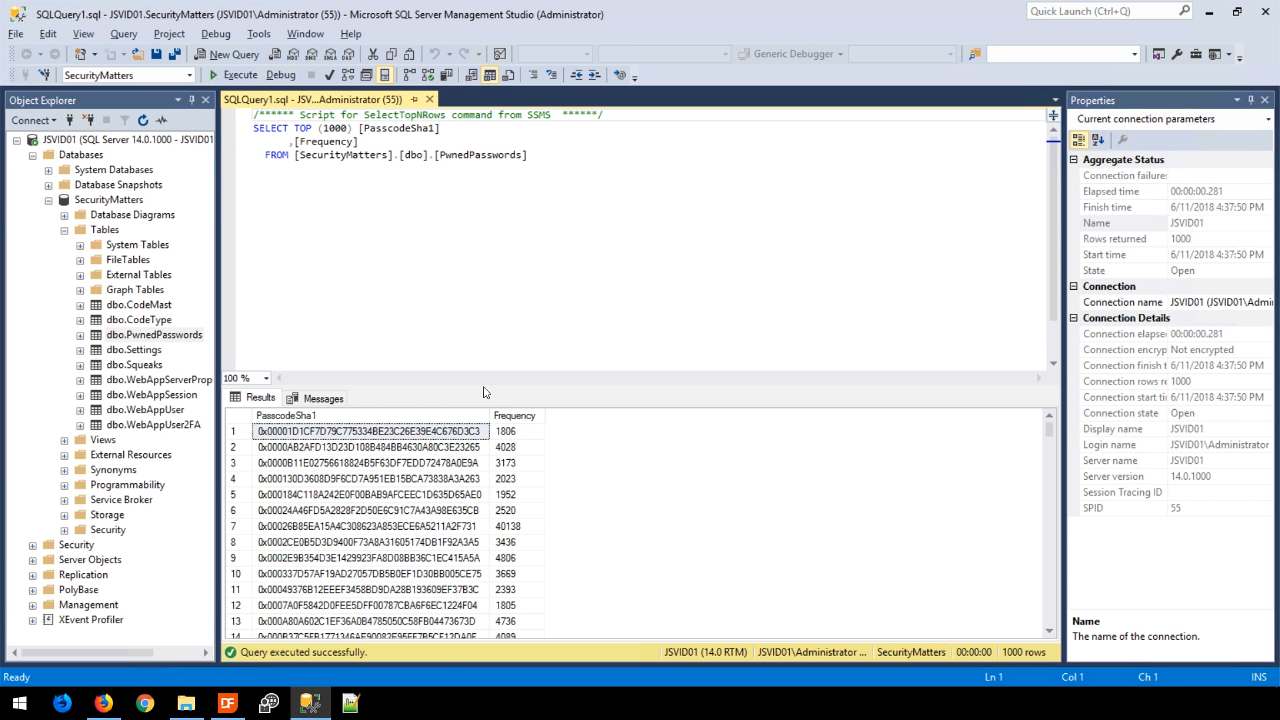
Viewing the table from the SQL Server Management Studio shows the type of data it contains: the binary hashes and their frequency.
CHALLENGE – whenever someone changes their passcode, create a sha1 hash, and check it against the list, and if it is included deny them the use of the code.