If passwords are stored as plain text, they can be abused. Therefore, they must be stored securely, which in this context means expensive to break. Dedicated password hashing algorithms use specific amounts of processing power to generate a passcode hash. Others also make sure that a certain amount of memory is needed.
To demonstrate some of this a view called, “Play with passcodes,” has been created in the SecurityBasics project. From the application screen, select VIEW from the top menu and then PLAY WITH PASSCODES.

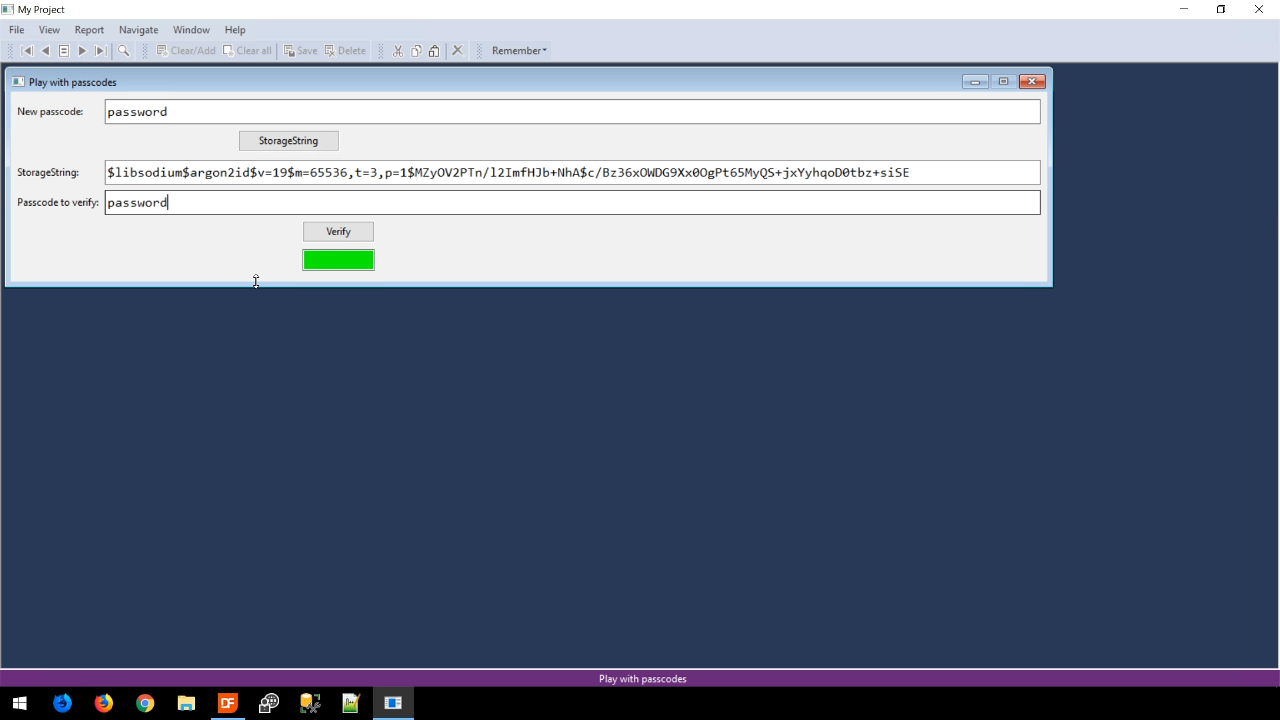
Entering a password into the ‘Password’ field and pressing the STORAGESTRING button (actual method in the security library that can be used) results in a string in the ‘StorageString’ field. The beginning portion of the string shows that libsodium was used as the engine and argon2id is the algorithm. The rest of the string contains some parameters, a salt value, and the resulting hash value.

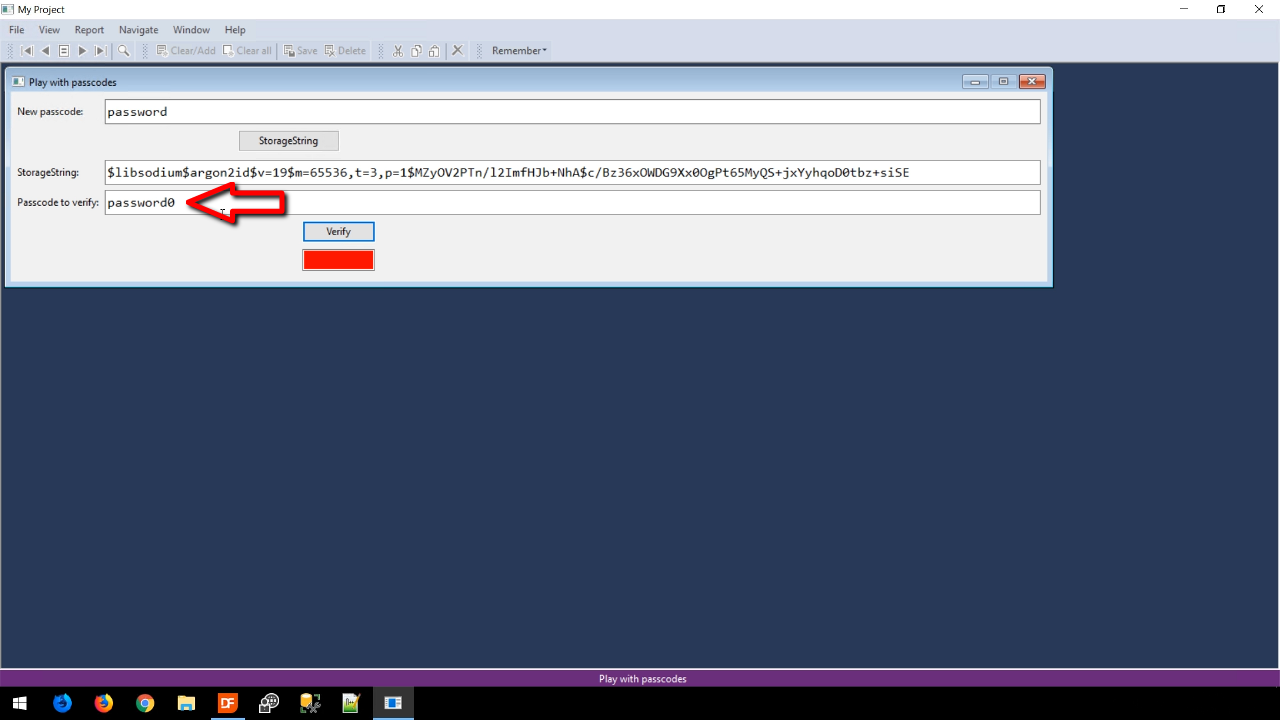
Pressing the button numerous times will always result in a new string. When entering the ‘Passcode to verify’ the password needs to be an exact match and is case-sensitive. If it is the result box will show green with the ‘Verify’ button is pushed. If not, it will show as red.
To view the code of how this was done, expand ‘Views’ under ‘SecurityBasics.src’ in the ‘Workspace Explorer’ panel on the right, and select ‘PasscodePlayground.vw.’
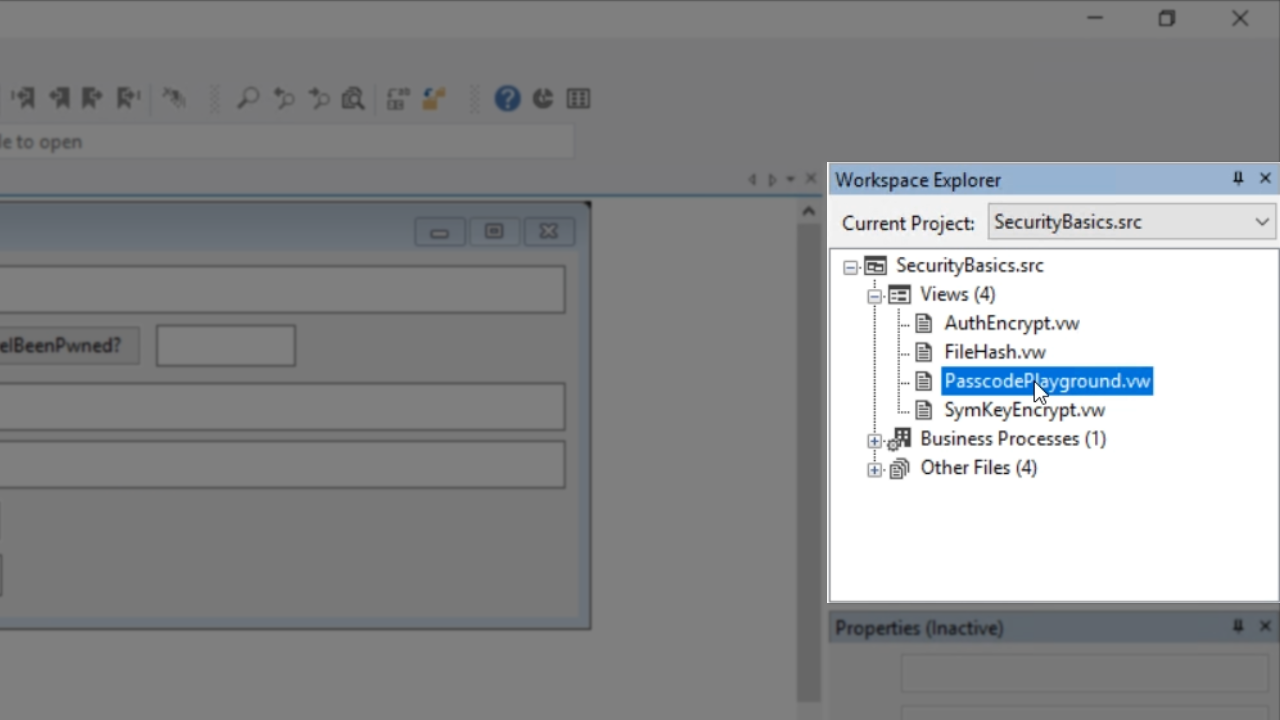
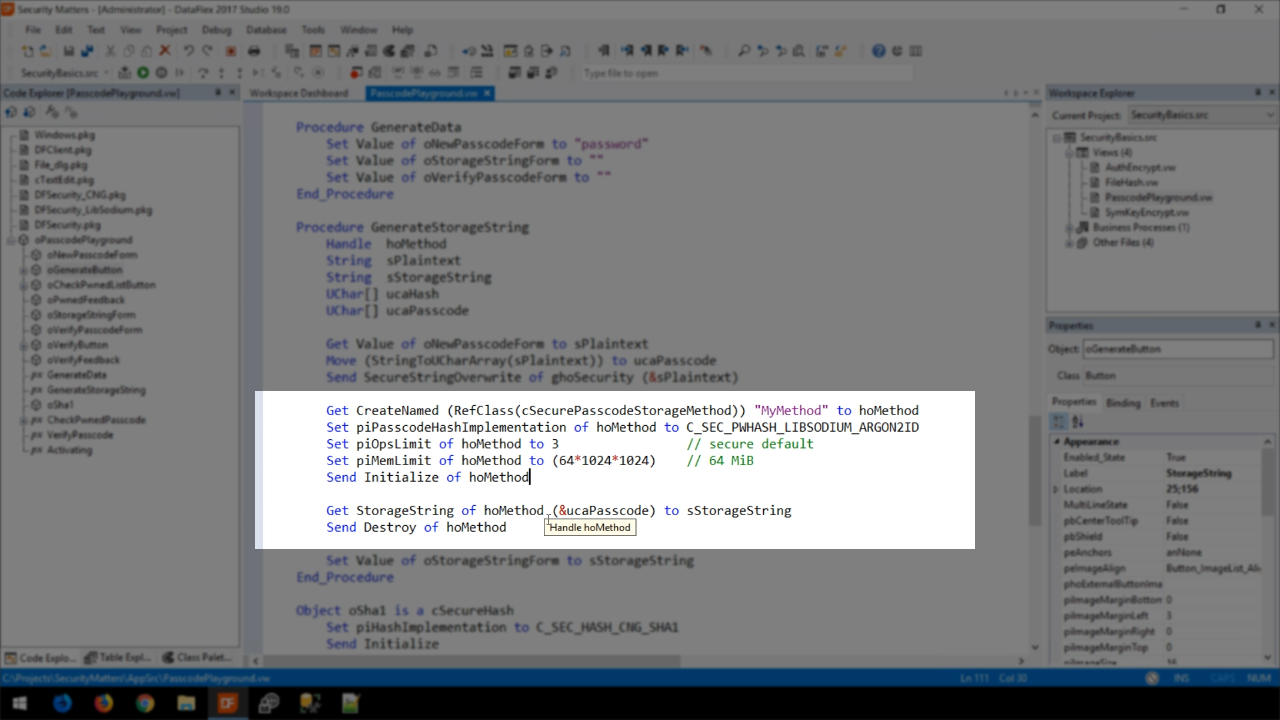
To look at the code for the button, expand ‘oPasscodePlayground’ in the ‘Code Explorer’ panel on the left, and select ‘oGenerateButton.’
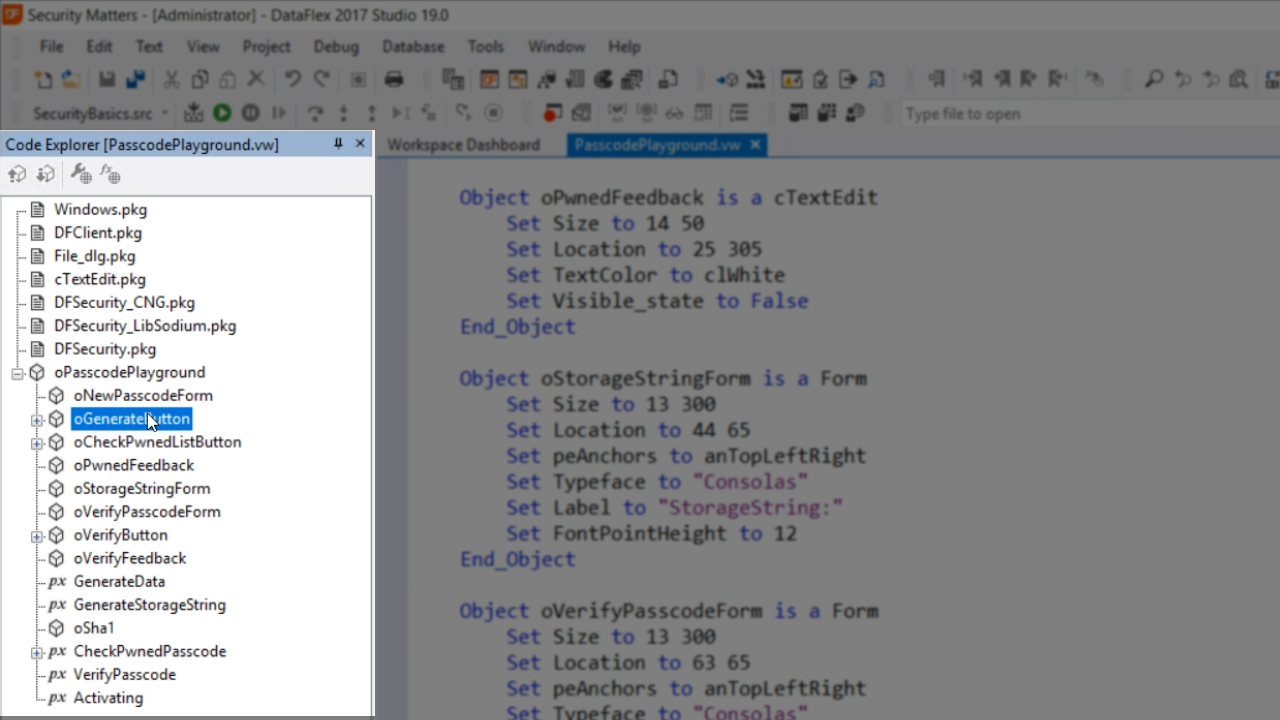
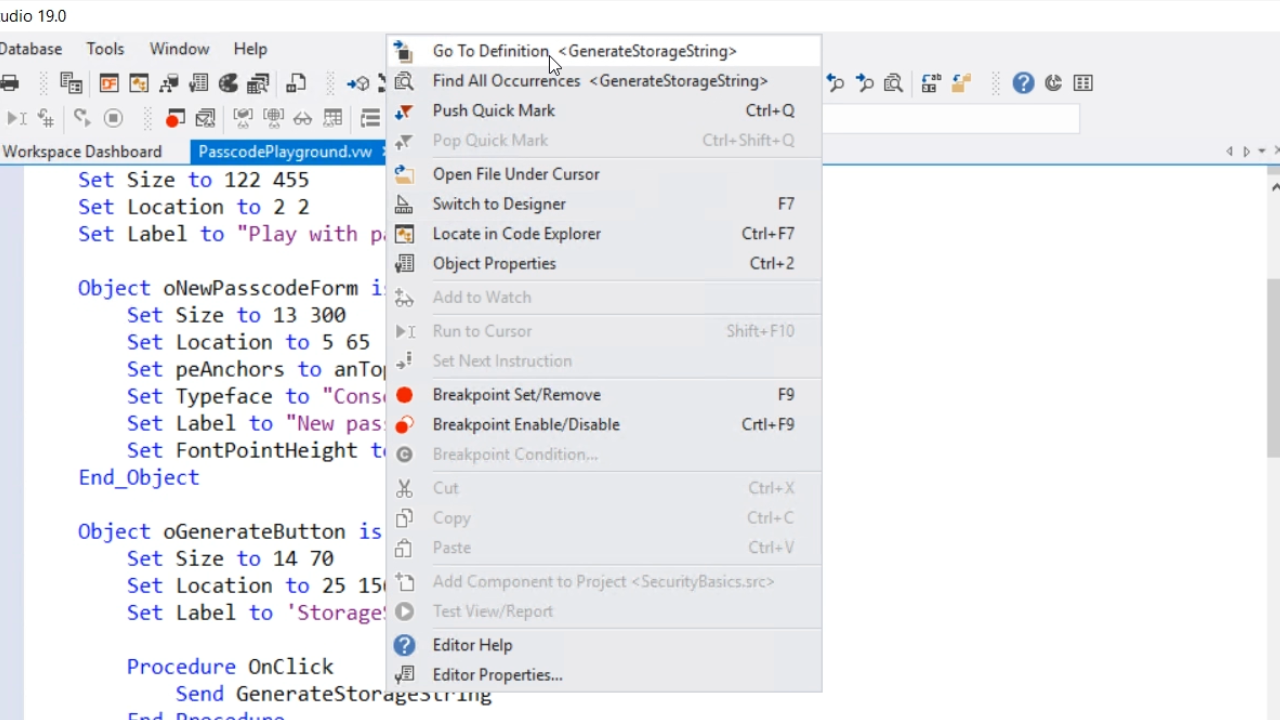
The code shows that GenerateStorageString is called. Right clicking on it and selecting ‘Go To Definition’ will bring up the code showing what it does.
Firstly, it gets the plaintext password and it is turned into a uChar array.
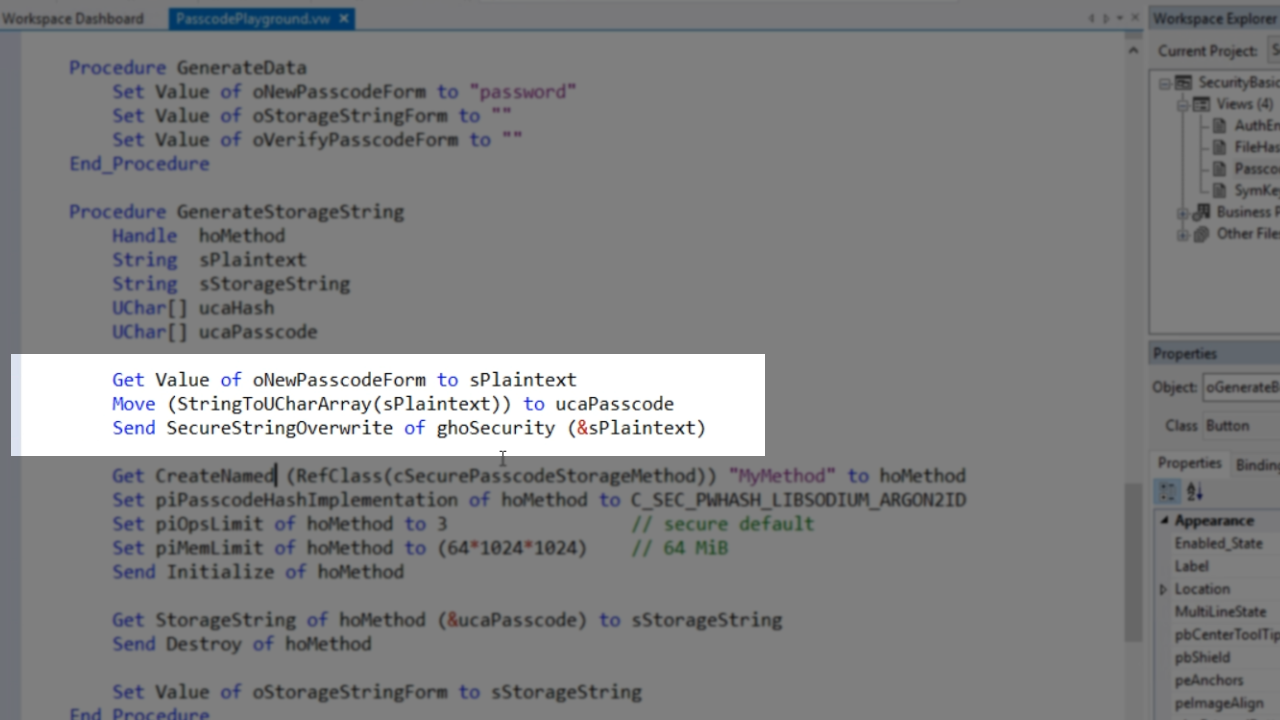
Then a new object is created from the cSecurePasscodeStorageMethod class. Next the piPasscodeHashImplementation is set. In this example, it is set to C_SEC_PWHASH_LIBSODIUM_ARGON2ID. Then the number of operations is set; here it’s set to 3. This is a rather secure default, but different algorithms may require this to be set to a much higher number. The piMemLimit, which is the amount of memory used, is then set. Not all algorithms support this, but Argon2 does. Then the object is initialized. Following all of that, the storage string of the method is retrieved using the uChar array to create the storage string – Get StorageString of hoMethod (&ucaPasscode) to sStorageString.
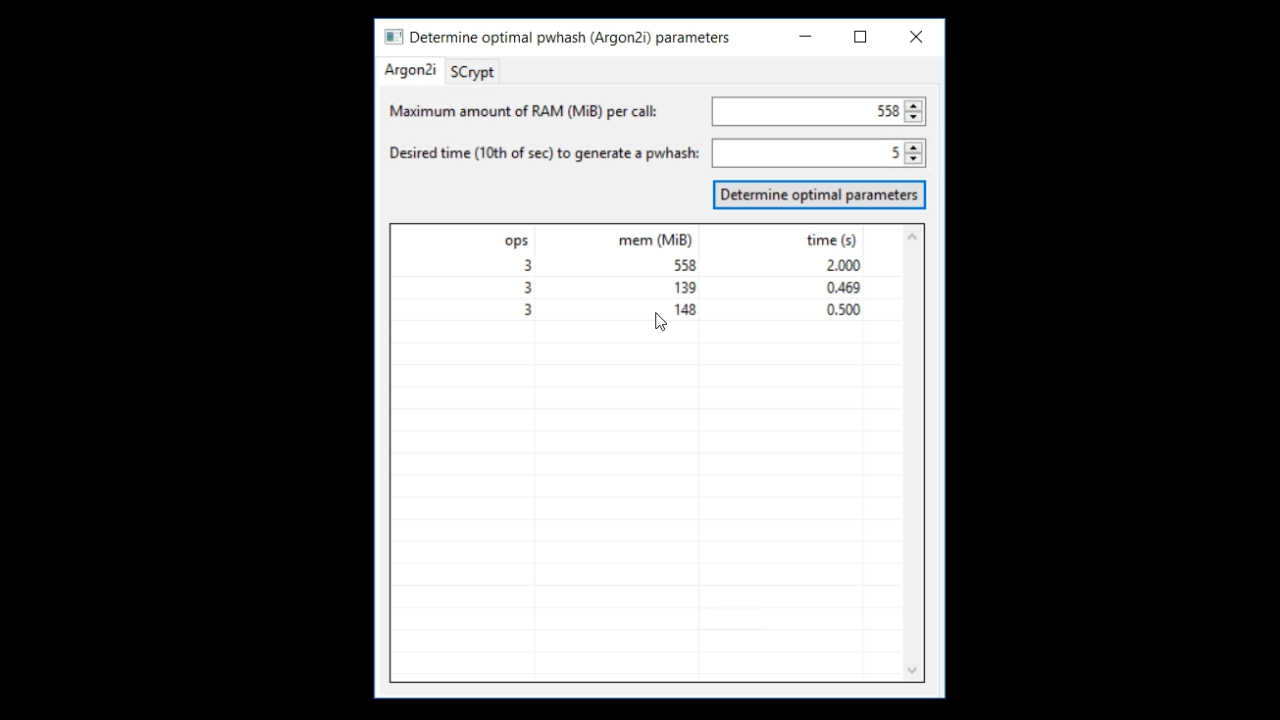
To help developers determine the number of operations (piOpsLimit) and the amount of memory (piMemLimit) to require a project template has been developed within DataFlex. To use it, navigate to FILE > NEW > PROJECT from the top menu.